The Initial Situation - Application Forwarding from Ostendis
The Ostendis E-Recruiting solution enables the HR department to forward applications to department heads, team leaders, management members, etc. for evaluation.
They then receive an email with a login link that leads directly to the Ostendis account of the person concerned and thus to the forwarded applications.
The Problem
Only one person can work in an Ostendis account at a time. Our system registers all simultaneous accesses and automatically logs out the user who logged in first from the system.
This leads to the following message:
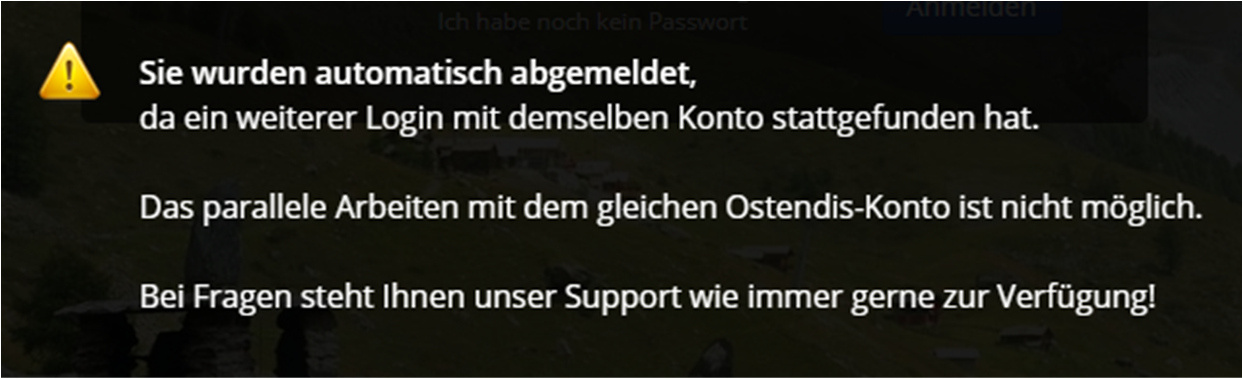
The Cause
Either another person has actually logged in with the same Ostendis account, or your company is using a progressive email security solution such as Microsoft Advanced Threat Protection (ATP). This checks links in an email when the email is opened by having the Microsoft security system itself click on the login link to analyze its behavior.
When an Ostendis user clicks on the login link in the email, it’s possible that Microsoft also clicks on this login link. This leads to automatic logout and the above message for the Ostendis user.
The Solution
There are two solutions to fix this problem:
Solution 1: Force login with email address and password instead of login link
Solution 2: Set up a rule in Microsoft 365 (Office 365)
Procedure for Solution 1
This solution can be easily implemented by an Ostendis company administrator. They only need to activate the following marked option in Ostendis under ‘Company’ -> ‘Settings’:
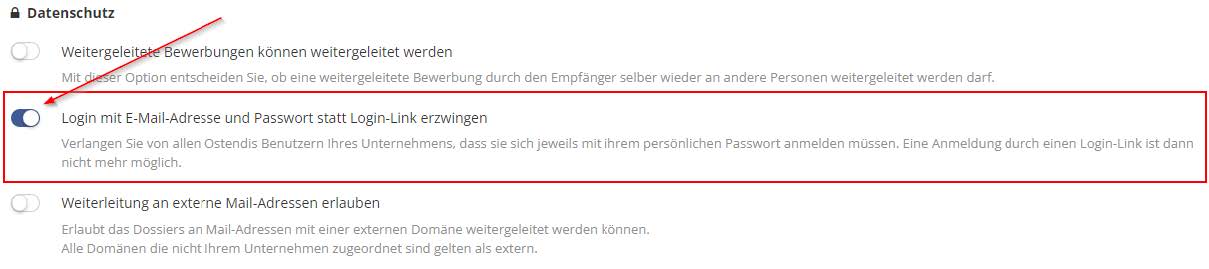
This means that logging in by simply clicking a login link in a notification email is no longer possible. Ostendis users will be required to enter their Ostendis login credentials. If someone hasn’t defined a password yet, they will enter the system with the login link and must then set a password.
This solution offers three advantages:
- It can be easily implemented by an Ostendis company admin.
- It increases overall access security to Ostendis and the sensitive information naturally stored in it, as a login link in an email can fall into the wrong hands more quickly (e.g., accidental forwarding of an email) than a password.
- The original problem of Ostendis users being automatically logged out of Ostendis from time to time no longer occurs, as Microsoft (or ATP) can no longer log into the account since it is now mandatorily protected by a password, which Microsoft naturally doesn't know.
Procedure for Solution 2
The IT department of your company, or more specifically the Microsoft 365 administrator responsible for and authorized to manage Exchange, must make a system setting to prevent the ATP system from clicking on the link in the email from Ostendis.
What does Solution 2 for the problem look like in detail?
With the following instructions, you can set up the required mail flow rule in the Microsoft 365 Admin Center. Since most IT departments install and administer their systems in English, the instructions are in English:
- Login to Microsoft 365 Admin Center with an Exchange admin account
- Go to “Exchange” in the left menu under “Admin centers”
- Go to “Rules” in menu “Mail flow”
- Click “+ Add a rule” and “Create a new rule”
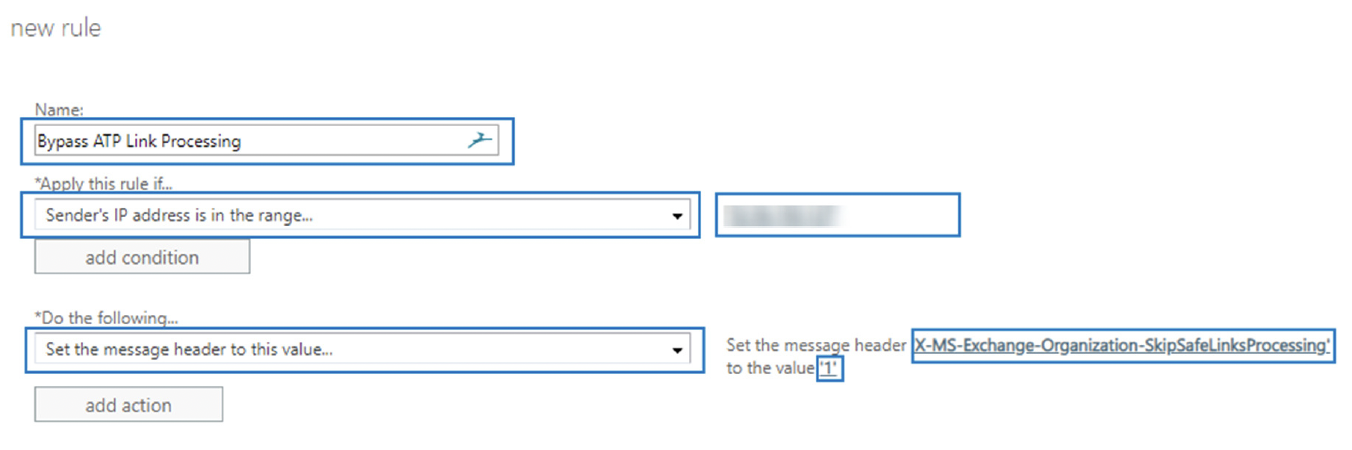
- Give the rule a name, e.g. “Bypass ATP Link Processing”
- Under “*Apply this rule if…” select “The Sender…” > “IP address is in any of these ranges or exactly matches…”
- Enter the Ostendis mail server IP address 94.231.81.6, and hit “+”
- Under “*Do the following…” select “Modify the message properties…” > “set a message header” and enter the following:
- Set the message header: “X-MS-Exchange-Organization-SkipSafeLinksProcessing”
- to the value: 1
- Hit Save
Do You Have Further Questions?
If you have questions, our support team is happy to help you via email or phone.
Email: [email protected]
Phone: +41 62 511 20 88
Wie hilfreich war dieser Beitrag?

